
Many security experts say a breach is only a matter of "when" not "if". Imagine the sinking feeling of finding out your company has been compromised in this way. However, you can be proactive in defending yourself, and Qualys CTSO and VP solutions architect EMEA and APAC Richard Sorosina brings practical advice to help.
When it comes to cybersecurity the bad guys have an advantage; they only need to be successful once to breach your defences while you need to protect against everything all the time. Fortunately, you're not in this fight alone, with many solid, robust companies dedicated to combating cybercrime and protecting your company.
One of these is Qualys, a leading provider of cloud-based security and compliance solutions. Qualys offers a comprehensive suite of products designed to simplify the management of IT security and compliance for organisations of all sizes and help them protect their critical IT assets against ever-evolving cyber threats. Richard Sorosina took time from his busy schedule to speak with iTWire about this vital topic.
Cyber risks are continually evolving. Ransomware has been big, and continues to enjoy a lot of success in compromising companies. So too are business email compromises. However, they don't stop with these. "Supply chain risk is a major concern, increasingly dominating discussions among cybersecurity leaders," Sorosina says. "At a recent CISO luncheon, nearly every participant highlighted third-party risk, whether in the context of software supply chains or supplier relationships. Since 2022, breaches via supply chains have become more common than those from malware."
{loadposition david08}
"In response, major businesses are proactively managing third-party risks by conducting unannounced security assessments on their suppliers, requiring them to document and demonstrate the effectiveness of their security controls. This proactive approach underscores the critical importance of securing the entire supply chain to mitigate potential vulnerabilities."
It's a lot to take in, and the beleagured IT Manager at many a company has so much to deal with already, bedore adding the continual threat of cybercrime. Yet, you can't stick your head in the sand. You can't assume because you're not aware of hacking going on in your network that it doesn't happen.
While the sage wisdom over centuries has been "no news is good news" Sorosina says "no news is definitely not good news in cybersecurity."
"If a CISO isn't hearing about any issues, it probably means there's a lack of visibility," he says. "In today's environment, constantly monitoring and addressing risks is essential. A silent network can indicate poor communication or unreported problems. Without proper visibility, you can't measure, communicate or eliminate threats. So, not hearing anything should be a cause for concern, not relief."
Thus, to start being proactive about securing your environment and protecting your company and its people and assrts, you need to get a handle on how exposed you are, and to separate signal from noise.
"To understand their exposure, businesses need to start by understanding the known and unknown cyber risk across their internal and external attack surface," Sorosina says. "To do this requires identifying and mapping their assets. This is the foundation for an accurate risk assessment. It’s what we call the measure phase."
One size doesn't fit all, either. "A key part of this is understanding context: software companies must protect intellectual property, financial services need to safeguard payment data and healthcare providers must prioritise patient data."
"Similarly, compliance and regulatory requirements are crucial in understanding risk. Ignoring vulnerabilities can lead to non-compliance, resulting in fines or legal action. Additionally, integrating threat intelligence from third-party sources enhances vulnerability understanding. For instance, if there's a surge in attacks on specific software, companies using that software should prioritise immediate patching."
What's more, "effective cybersecurity hygiene also includes identifying and monitoring end-of-life software," Sorosina says.
"Continuous asset monitoring, underpinned with best practices like CIS benchmarks, especially in cloud environments, is critical. It means that risks can be captured and prioritised, and it ensures timely and targeted remediation. Qualys' expertise in identifying active vulnerabilities helps pinpoint the most dangerous threats."
Sorosina adds, "timely remediation is essential. New vulnerabilities can be weaponised within 19 days, while organisations typically take 30 days to patch them, creating an exploitable window for cybercriminals."
"Businesses need efficient detection, management and mitigation processes. A robust patch management program, aligned with a risk management strategy, ensures critical vulnerabilities are promptly addressed."
To sum up, Sorosina's advice is that effective cybersecurity requires a multi-layered approach. You must understand and map assets, integrate contextual information, continually monitor, and remediate swiftly.
Oh my, that's a lot, but, Sorosina says, "by prioritising risks based on their potential impact and maintaining robust cybersecurity hygiene, businesses can protect against evolving threats and maintain organisational resilience."
Here at iTWire we strongly believe what gets measured gets improved. We asked Sorosina if it really is possible to measure your security risks, and consequently, the impact of your risk management efforts to remediate them. And can we get close to real-time?
Sorosina says measurement is key in cybersecurity, but "you can only measure your risk if you fully understand the risks in your business. This means having full visibility into your assets and understanding the potential impact. This will vary for every organisation; two seemingly identical companies will likely have different risk appetites and data protection needs."
"To get anywhere near real-time capabilities organisations need a comprehensive, multi-layered approach. Only by having full insight into your assets, risk appetite and context will you have the right systems to promptly address threats as soon as they are detected."
A particularly component of the Qualys portfolio is Qualys Vulnerability Management, Detection and Response (VMDR), which helps organisations detect and prioritise vulnerabilities across their global IT environment, keeping you informed of where risks lie.
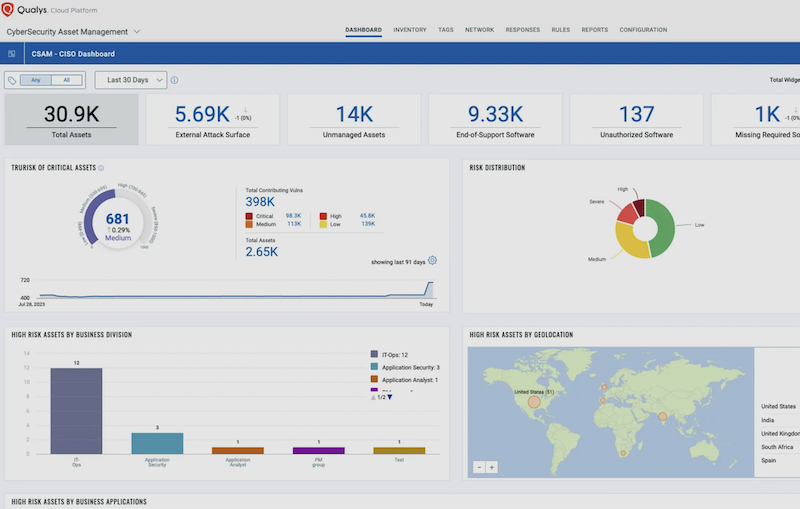
"Tools like Qualys VMDR can help by offering integrated capabilities for asset management and cybersecurity," Sorosina says. "This includes identifying end-of-life software, spotting unauthorised software and maintaining a comprehensive software inventory. VMDR also incorporates threat intelligence to contextualise vulnerabilities, helping prioritise remediation. External scanning capabilities further enhance this by identifying vulnerabilities exposed to the internet, a common breach point."
With these under our belt - an assessment and mapping, and a tool to identify vulnerabilities, the next step is to ensure these risks are scored appropriately. You don't want to invest all your time in mitigating an unlikely, low impact potential exploit when there are many other much riskier problems.
"As an organisation you need to evaluate the frameworks you are looking to implement," Sorosina says. "Not all frameworks are suitable for every business and it will also depend on your maturity, risk appetite, the skills within teams to implement it, and so on. Implementing and aligning to a risk framework will improve your security posture, but the wrong framework can be a hinderance. For instance, the NIST Cybersecurity Framework (CSF) is very comprehensive and robust. However, its complexity can pose implementation challenges for smaller companies. So, when choosing a risk assessment method, enterprises must consider the types of factors mentioned above to ensure the chosen framework aligns with their specific needs."
There are a range of tools, but obviously, Qualys is a serious contender. It serves over 10,000 customers in more than 130 countries, including a majority of the Forbes Global 100. The company protects millions of IT assets and endpoints globally, ensuring that organisations can effectively manage their security and compliance posture.
The backbone of all Qualys’s services is the Qualys Enterprise TruRisk Platform. Comprising 20+ powerful apps seamlessly integrated in a single, unified platform, it helps organisations to measure their cyber risk and gain instant visibility into all their IT assets - on premises, in clouds and at remote endpoints; to communicate and continuously assess their security and compliance posture; and to eliminate the most critical vulnerabilities with easy-to-use workflows that help unify Security and IT teams.
According to Sorosina, "Qualys empowers companies to identify all their assets and accurately measure associated risks within their organisational context. This comprehensive risk assessment enables businesses to effectively mitigate identified threats. In addition, Qualys provides precise risk data, facilitating clear communication with boards and stakeholders, enhancing their understanding of the company's risk landscape and supporting the development of a robust and meaningful cyber risk strategy."
Some good examples of Aussie success stories with Qualys include Australian Payments Plus (AP+).
"It was created from the merger of Australia's top payment organisations – BPAY Group, EFTPOS, and NPP Australia," Sorosina says. "AP+ handles billions of transactions annually, so safeguarding sensitive personal and financial data and maintaining public trust are a top priority."
"With BPAY having used Qualys over the past decade, AP+ turned to Qualys using VMDR with the Enterprise TruRisk Platform, an all-in-one, enterprise-grade cyber risk management tool, and integrated asset management apps to strengthen its cybersecurity across 2,000 diverse cloud and on-premises assets. With VMDR, AP+ can manage vulnerabilities, detect threats and respond quickly across its entire infrastructure. Additionally, Qualys Cloud Agents scan everything weekly—laptops, AWS servers, you name it—pinpointing vulnerabilities and prioritising fixes.
This proactive approach means AP+ can tackle high-severity risks promptly and it boosts operational efficiency. Automating with VMDR® cuts down the manual workload by several weeks each year, freeing up its lean security team to focus more on strategic analysis rather than data collection."
"Plus, Qualys VMDR means they can stay on top of missing patches and outdated software, and use the self-service vulnerability reports with developers, helping increase agility in responding to regulatory changes and tech updates."